How to Remove Pc Doctor From Windows 10
If you want to know how to remove ransomware from your Windows PC, we've got good news and bad news. The good news: It's not simple, but it's possible. The bad news: It's not always possible. Ransomware programs and attacks are continuously growing more sophisticated. As a result, victims are having more difficulty cleaning their computers and recovering their files.Can ransomware be removed?
Depending on the type of attack, ransomware removal varies from simple to impossible. For instance, scareware attacks install malicious software programs you can uninstall in minutes. But the most common variants, known as filecoders or encryption ransomware, are far scarier: They encrypt your valuable files. Even if you manage to remove the malware itself, you still need to decrypt your data to access it. In this case, rather than deleting or corrupting your files or stealing your identity, the attacker's encryption holds your files hostage until you pay for a decryption key.
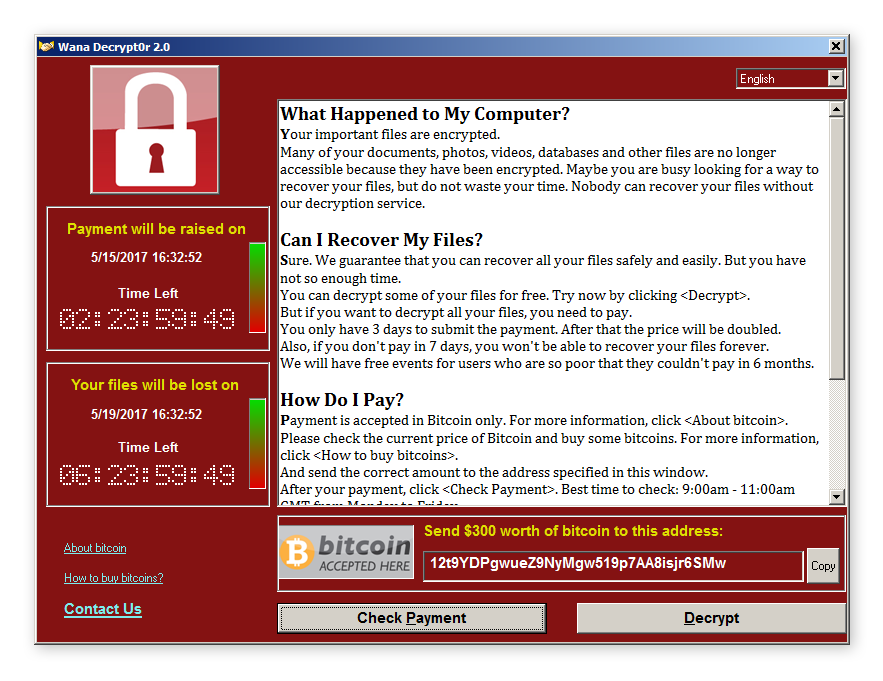
Every filecoder has its own method of encryption, which means you can't simply remove it like other forms of malware. To avoid being studied and decrypted, most ransomware programs delete themselves after a set period of time. When they don't, you can usually use Avast Free Antivirus to remove them. Getting rid of the malware is clearly a good thing for you and your Windows PC. And although your files may still be encrypted, at least you're stopping the ransomware virus from spreading to other computers and devices through public and private networks.
If you know which type of ransomware your PC has, you might be able to find a legitimate ransomware decryption tool to recover your files. However, proceed with caution during your search – many ransomware variants use enterprise-grade encryption that is impossible to crack. Also, there is a criminal element that preys on people in this situation, tricking their victims into downloading more malware with promises of fast and effective decryption.
An ounce of prevention is worth a pound of cure
You can prevent ransomware from affecting you and your PC with minimal effort. Back up your files and your PC's operating system (OS) on a regular basis. You can use a cloud storage solution like Dropbox or Google Drive for your files, and a flash drive for your OS as well as your files. Whichever solution you choose, don't ever keep your backups on the same Windows PC because ransomware can infect them along with your originals.
To reinforce your PC's defenses against this type of malware,Avast Free Antivirus includes highly effective protection against ransomware.
STEP 1: Immediately isolate infected devices
The first thing to do if your Windows PC gets ransomware is find and disconnect all the infected wired and wireless computers and other devices on your network. This will stop the ransomware from spreading and taking more of your computers, tablets, and/or smartphones hostage.
During this procedure, also disconnect everything connected to the devices on your network, including:
-
Shared or unshared network drives
-
External hard drives
-
Flash drives
-
Cloud storage accounts
To complete this step, check whether any of these were connected to the infected PC. If you suspect they were, you will need to check their systems for ransom messages as well.
STEP 2: Identify the type of ransomware attack
Next, find out which strain of ransomware you're dealing with. This knowledge could help you find a fix.
The most problematic types of ransomware are filecoders like WannaCry or CryptoLocker. Other variants, like screenlockers are generally easier to remove. Here's a brief overview:
-
Filecoders encrypt and lock files on your PC. The cybercriminals behind this type of ransomware demand payment for decryption keys usually by a deadline or your files could become damaged, destroyed, or permanently locked. Around 90% of ransomware strains are filecoders.
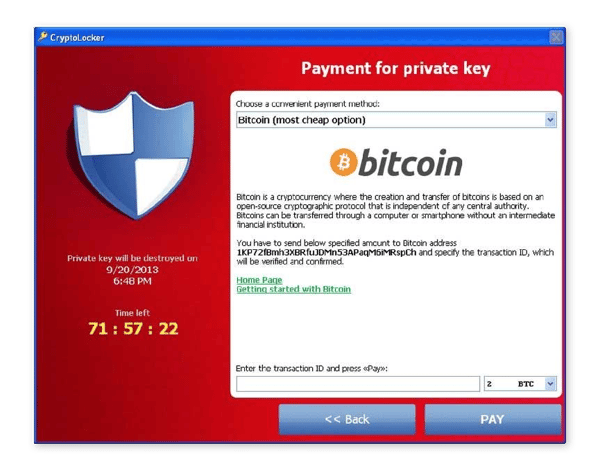
-
Scareware typically bombards your PC with pop-up ads for a fake security tool that demands payment in exchange for fixing bogus PC issues. The easiest type of ransomware to get rid of, it's the least troublesome of the bunch.
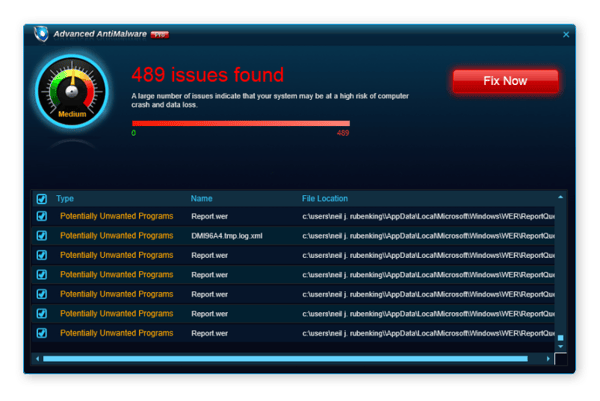
-
Doxing-related ransomware involves an email or message telling you cybercriminals have your usernames, passwords, emails, and/or instant messages – and will make them public unless you pay a fee. Our free Avast Hack Check lets you know if any of your passwords have actually leaked or been stolen.For stronger protection, use our personal info monitoring tool, Avast BreachGuard.
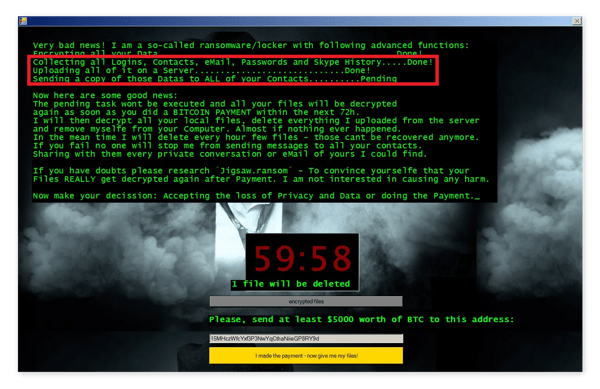
-
Screenlockers do exactly what the name says: They lock your screen, blocking access to your machine. They tend to look like they're from a government institution like the US Department of Homeland Security or the FBI and say you broke the law and must pay a fine to unlock your PC. Screenlockers are now more common on Android devices than Windows PCs.
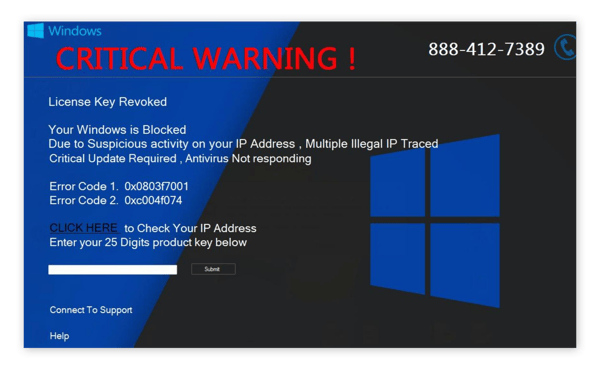
While the vast majority of ransomware attacks solely target Windows PCs, all four variants listed above can infect Macs, iOS devices, and Android devices.
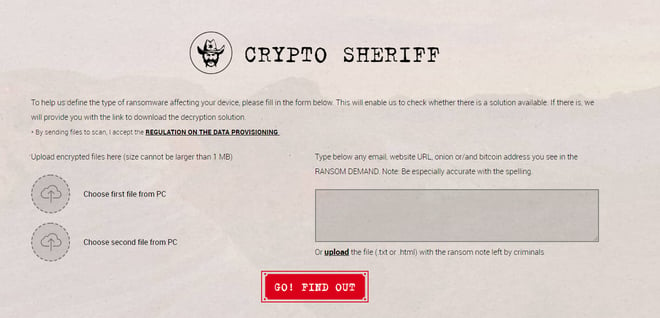
Use Crypto Sheriff tool to identify the ransomware type
To help you determine the type of ransomware on your machine, we recommend using No More Ransom's Crypto Sheriff. Provided by Europol's European Cybercrime Center, this handy tool checks files the attacker has encrypted and the ransom note. If Crypto Sheriff recognizes the encryption and has a solution, it gives you the link to download the decryption program you need.
Visit tech forums to learn more about ransomware types
You can also visit PC troubleshooting and tech support forums to find information about the ransomware variant you want to remove. Even if it's new, you might find a thread that offers a fix, or a thread where forum members are working towards a solution.
Some ransomware infections will rename your files and file extensions (for example: .exe, .docx, .dll) after encrypting them. When you visit tech forums for help, search for the names and extensions of your encrypted files; each can help guide you to discussions about the strain of ransomware you wish to get rid of.
We recommend you look in these forums:
-
Bleeping Computer Forums
-
Computer Hope Forum
-
Microsoft Community
-
Reddit (r/Ransomware)
STEP 3: Remove ransomware malware
Now it's time to get rid of the underlying malware that's holding your PC hostage. You have four ransomware removal options for Windows 10, 8, and 7:
-
Check if the ransomware has deleted itself (which it often will)
-
Remove it with Avast Free Antivirus
-
Have our experts at Avast Premium Tech Support get rid of it
-
Remove the malicious program manually
Option A: Check if the ransomware program deleted itself
It is highly probable that the ransomware on your PC will actually remove itself after encrypting your files. Cybercriminals don't want their malicious software to leave any clues that could help create decryption tools for that strain. You can use Avast Free Antivirus to scan your machine for ransomware.
Option B: Remove the malware with Avast Free Antivirus
Avast Free Antivirus can detect and delete many types of ransomware programs quickly and easily. It will also help keep your Windows PC safe from all types of cyberattacks in the future.
Option C: Let Avast Premium Tech Support get rid of ransomware for you
You can contact our experts at Avast Premium Tech Support (APTS) and ask them to delete the ransomware malware. APTS is a paid service offering 24/7 support for all your computer and software issues. The team can help you with ransomware removal – however, they will not be able to recover encrypted files.
Option D: Remove the ransomware manually (ADVANCED PC USERS ONLY)
In most cases, you can remove ransomware from your Windows PC using options B and C above. If you want to clean your computer yourself, we advise you to first visit the online forums we mentioned above. We're unable to provide instructions on how to remove all the programs behind ransomware attacks on your own – there are simply too many of them. You'll be able to learn much more from forum members' experiences and guidance.
STEP 4: Recover your encrypted files
With the underlying malware gone, you're now ready to begin the file recovery process. Here are a few methods that can help you regain access to your encrypted files.
Option A: Restore your system from a backup
If you've been backing up your computer's operating system, you can restore your system and files easily and handle the scareware, screenlocker or filecoder that infected your PC. Once you remove the program that's keeping you from opening Windows or running programs, encryption will not spread through your machine and network.
While screenlockers make up the minority of ransomware cases, you should still give your machine's System Restore function a shot. Doing so rolls your PC's system files and programs back to a previous state. While the feature is enabled by default, it's a good idea to double-check this, especially if you're using a shared or previously owned computer.
You can also try to access shadow copies of your files, which will help you restore them. If this doesn't work, give restoring previous file versions a go. Windows 10 and Windows 8 have a File History feature that makes this easy; Windows 7 requires a little more effort, but the method is still straightforward.
You can only use shadow copies to recover files when you're dealing with a basic filecoder. This method won't really help you in a doxing scenario because the threat is different – you may be able to recover your files, but the hacker has your personal data and is demanding payment in exchange for keeping it private.
In some cases, the ransomware on your PC may have only hidden your files. You can recover them easily in all versions of Windows.
In Windows 7, the path is Computer > Press Alt and select Tools > Folder Options and select View tab > Select Show hidden files, folders, and drives > Click OK .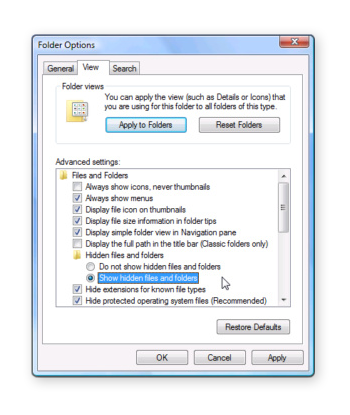 In Windows 10 and 8, simply open File Explorer, select View, and check Hidden items .
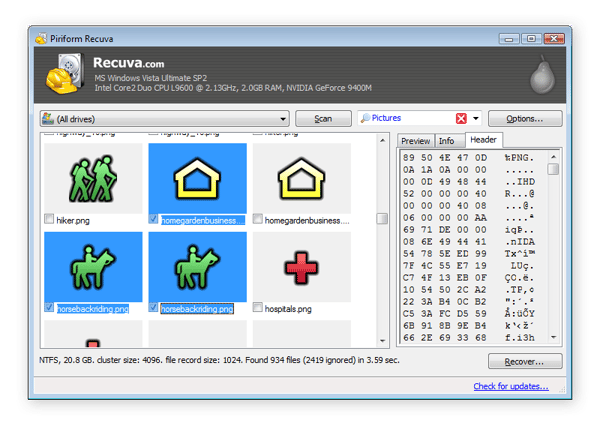
In Windows 10 and 8, simply open File Explorer, select View, and check Hidden items .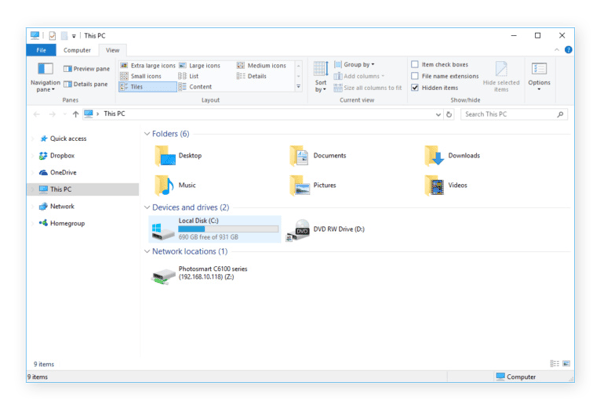 Finally, you can try using CCleaner's file recovery software Recuva, which will also help you recover deleted or lost files.
Finally, you can try using CCleaner's file recovery software Recuva, which will also help you recover deleted or lost files.
Option B: Use decryption tools
If you've identified the ransomware as a filecoder that has encrypted your files, and if you know the specific strain of encryption, you can try to find a decryptor that could help you regain access to your files. Our free Avast decryption tools provide information about some known types of ransomware, including filename changes and ransom messages, and a free downloadable decryption program for each strain. (Note: most of these tools are for Windows PCs).
Unfortunately, most ransomware strains have yet to be decrypted, so in most cases there won't be a tool capable of unlocking your files. In this unfortunate scenario, your options are limited to restoring files from a backup (if you have one), or waiting until someone releases a free decryption tool for the particular ransomware strain on your PC.
Option C: Don't pay the ransom and don't negotiate
If you've followed all the steps we've listed and still can't unlock your files, we recommend you wait for the release of a decryption tool for the type of ransomware that has infected your computer. In some cases, cybercriminals reveal parts of their code that can help create a solution.
We understand the urgency of the situation, but we strongly recommend not paying the ransom or negotiating with your PC's hijacker. Payment only supports ransomware attackers, motivating them to continue their activities and develop new strains. In some cases, ransomware payments could also be funding other illegal activities.
Finally, please be aware that criminals don't always remove ransomware, unlock your computer, or give you the decryption tool for their strain when you pay them. Most of them want a reputation for keeping their word so their victims are more likely to pay them, but it's not uncommon for cybercriminals to collect payment and disappear or send decryptors that don't work. In some cases, you may end up paying a completely different criminal.
Common Questions
Here are some of the most frequently asked questions concerning ransomware.
How did my PC get ransomware?
In most cases, ransomware victims accidentally infect their computers. Awareness of the traps and tricks that cybercriminals use is vital to keeping your system and files safe. Ransomware can infect your PC when you:
-
Connect it to an infected network
-
Visit unsafe websites with dangerous or deceptive content
-
Open attachments in malicious emails
-
Click on malicious links in emails, social media posts, and instant messages
-
Install pirated content and software
Untrusted websites and fake emails often use slightly misspelled versions of their trusted and real versions. For example, supportapple.com (rather than support.apple.com) or ebay@reply.eba.com (rather than ebay@reply.ebay.com).
Outlook, Gmail, and other email clients have their own means of helping keep you safe from ransomware, but you should still keep an eye out for suspicious file extensions such as executables (.exe) and Microsoft Office files that support macros.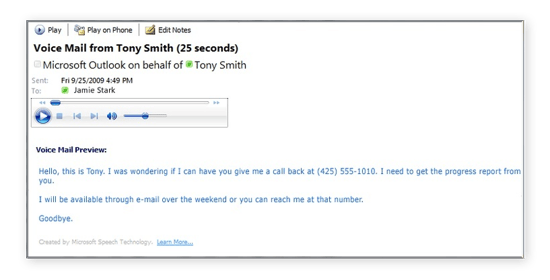 Social media networks such as Facebook, Twitter, and Instagram also do their best to keep their users safe from scams, but it's still in your best interest to remain vigilant before, say, participating in trending quizzes or clicking for more information about offers that seem too good to be true.
Social media networks such as Facebook, Twitter, and Instagram also do their best to keep their users safe from scams, but it's still in your best interest to remain vigilant before, say, participating in trending quizzes or clicking for more information about offers that seem too good to be true.
Instant messaging services like Skype, Whatsapp, and Slack offer great opportunities to meet and chat with new people. However, these services are also infested with scheming ransomware attackers, so be careful when accepting new contact requests, and don't click on links from strangers.
Finally, it's worth mentioning that all brands of Windows computers are vulnerable to ransomware. Whether you use a budget HP desktop, a mid-range Lenovo convertible laptop, or a high-performance Dell gaming laptop, every action in the list presented above can result in criminals taking your computer, files, and even your network hostage.
Do I need to pay a ransom to recover my files?
No, you don't need to pay it. We understand how fear and anxiety could cloud your judgement. You just want to get your files back as quickly as possible. So you may feel compelled to give in to the demands of your PC's hijackers.
But, really, you don't need to, and you shouldn't do it.
Since the first documented ransomware attack in 1989, the AIDS Trojan, cybersecurity experts have been urging victims not to pay the ransom. Their strongest argument is that payment does not necessarily mean the criminals will honor their part of the deal.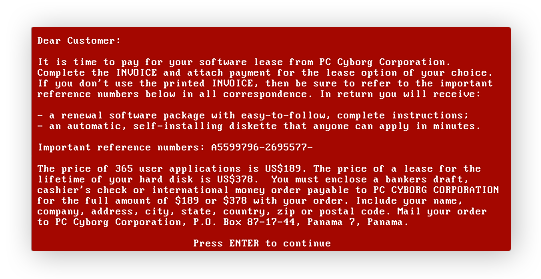
A 2019 report from the CyberEdge Group states that merely 19% of those who pay the ransom receive the decryption tool they need to recover their files. Ransomware payments are also helping fund the development of more sophisticated attacks; in some cases, they're indirectly funding other illegal activities.
If you've paid a ransom, contact your bank or payment service. While most attackers demand Bitcoin, your bank might be able to stop the transaction if you paid with your credit card. You should also contact your local authorities.
Is the data recovery process the same for all types of ransomware?
Ransomware has evolved rapidly and cybercriminals have developed an ever-increasing number of strains over the years. Every variant has its own attack vector and encryption technique. Cybersecurity experts have cracked several encryption methods, allowing for the development of decryption tools that help victims recover their files.
You can learn more about different ransomware strains in these articles:
-
What is WannaCry?
-
What is Locky?
-
What is Cryptolocker?
-
What is Cerber?
Unfortunately, ransomware creators continue to produce and spread new strains that have yet to be cracked. We're working hard to keep up with these and will continue to update our Free Ransomware Decryption Tools with as many new decryptors as we can find.
Set up your defenses against ransomware
We cannot stress enough how important it is to stop ransomware from accessing your computer in the first place. You can do this quickly and easily.
To start, back up your Windows PC and all your important files regularly, and not just locally – use the cloud and an external device, like a flash drive or an external hard drive. It's like going to your doctor for a checkup – it's one of those things we know we should do, but many of us don't until we have a problem.
You can strengthen your computer's defenses considerably with Avast Free Antivirus, which features a powerful ransomware shield.
When you stay vigilant, secure your PC, and back up regularly, ransomware will just be something you read about from time to time. As frightening as the stories may be, that sure beats dealing with it yourself.
How to Remove Pc Doctor From Windows 10
Source: https://www.avast.com/c-how-to-remove-ransomware-pc
0 Response to "How to Remove Pc Doctor From Windows 10"
Post a Comment